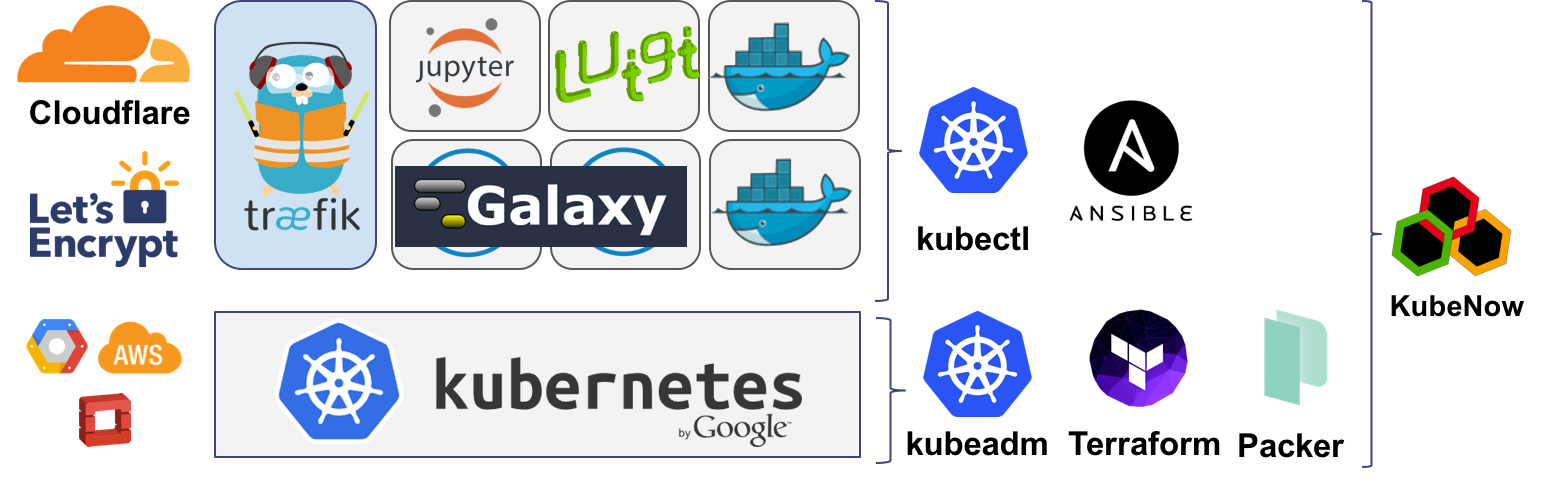
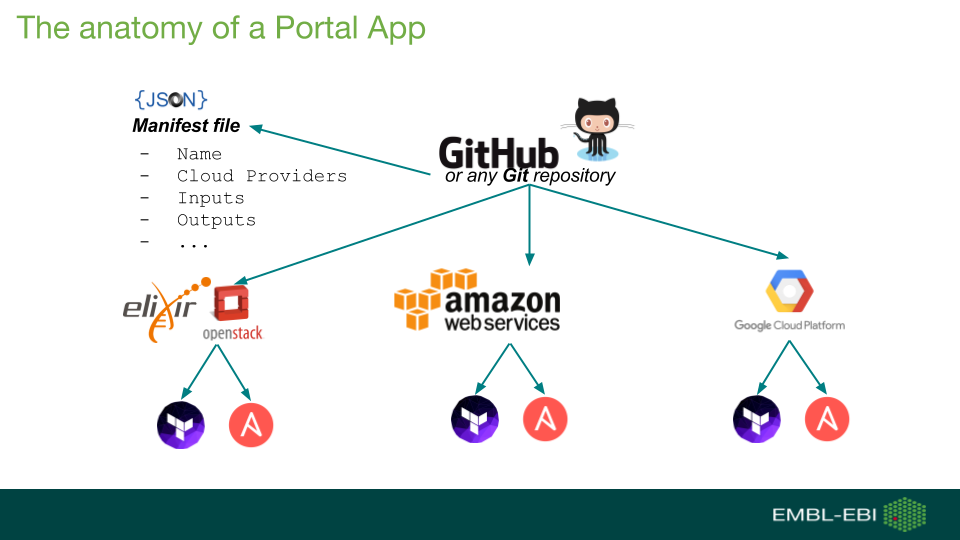
The workshop was held on March 29th at the Francis Crick Institute in central London.
Registration is now closed.
Programme now includes links to slides – updated 27/04/2022
| Timing | Plenary / Strand A Sessions Auditorium 2 | Strand B Sessions Auditorium 1 |
| 09:15 | Registration + teas/coffee | |
| 10:15 | Introduction | |
| 10:25 | Opening Plenary Chair: Cristin Merritt | |
| Reaching the cloud – Steven Chapman, University of Bath | ||
| Question time | ||
| 10:55 | Break – teas/coffee | |
| 11:15 | Session 1a – User Experiences Chair: Jay DesLauriers | Session 1b – User Experiences Chair: Cristin Merritt |
| Transitioning research computing workloads to the cloud: A thematic approach at Cardiff University – Tom Green, Cardiff University | Global Symmetry is important for the detection of abnormality in mammograms – Cameron Kyle-Davidson, University of York | |
| On the creation of a secure ‘serverless’ workflow between a Mapbox frontend and a SalesForce backend for the Tekkatho Foundation – Mike Jones, Independent Researcher | Capturing a Moment in the Cloud Workshop: How our perception and use of cloud computing has changed over time – Wil Mayers, Alces Flight | |
| Reducing time-to-science with self-service HPC and AI platforms in the Azimuth portal – Matt Pryor, Stack HPC | Crawlers, Bots, Flows, Lambdas, Glues and Autopilots: Applying AI and ML to Radiological Sensor Networks for Safety and Security – Peter Martin, University of Bristol | |
| Question time | Question time | |
| 12:15 | Lunch – buffet lunch | |
| 13:30 | Plenary (invited speakers) Chair: Cristin Merritt | |
| Developing and using the UK Biobank Research Analysis Platform, a large-scale Trusted Research Environment – Oliver Gray and Przemyslaw Stempor, UK BioBank | ||
| CLIMB-COVID: Cloud Infrastructure to Support the UK’s Covid-19 Response – Radoslaw Poplawski and Nick Loman, University of Birmingham | ||
| Question time | ||
| 14:15 | Session 2a – Trusted Research Environments Chair: David Fergusson | Session 2b – HPC in the Cloud – Applications Chair: Stig Telfer |
| TREEHOOSE: Trusted Research Environment and Enclave Hosting Open Original Scientific Exploration – Simon Li, University of Dundee | Twins in the Cloud: Simplifying the Deployment of Digital Twins for Manufacturing-as-a-Service – Jay DesLauriers, University of Westminster | |
| Data Safe Haven Classification and Trusted environments in the cloud: extending a Turing Django based application across multiple institutions – Rebecca Osselton, Newcastle University | An Introduction to DosNA: Distributed Numpy Arrays for High-performance cloud computing – Gabryel Mason-Williams, Rosalind Franklin Institute | |
| The Genes And Health TRE in the Google cloud – Vivek Iyer, Wellcome Sanger Institute | Maintaining versioned 3D digital designs using a hybrid and multi-cloud solution – Niall Kennedy, YellowDog | |
| Question time | Question time | |
| 15:15 | Break – teas/coffee | |
| 15:35 | Session 3a HPC in Cloud Chair: Alex Dibbo | Session 3b Covid & Cloud Chair: Stephanie Thompson |
| The PITHIA-NRF e-Science Centre – towards a Cloud-based Platform to support Ionosphere, Thermosphere, and Plasmasphere Research – Tamas Kiss, University of Westminster | Supporting UK Covid-19 surveillance with AWS Step Functions and Fargate at Wellcome Sanger Institute – Sam Proctor, Wellcome Sanger Institute | |
| King’s CREATE: a new research computing ecosystem and the journey so far – Matt Penn, King’s College London | Laying the groundwork for discovering the next novel coronavirus – Brendan Bouffler, Amazon Web Services | |
| Ensuring fairer access and reducing obstacles to research in fixed capacity clouds – Paul Browne, University of Cambridge & Pierre Riteau, Stack HPC | Cloud-based nonequilibrium simulations to investigate regulation and environmental effects in the SARS-CoV-2 spike protein – Sofia Oliveira, University of Bristol | |
| Question time | Question time | |
| 16:35 | Reconvene in Auditorium 2 … | |
| 16:45 | Final Plenary Chair: James Grant | |
| DRI Update – Justin O’Byrne, UKRI Digital Research Infrastructure | ||
| 17:05 | Sum-up, feedback, next steps | |
| 17:10 | Reception – drinks, light refreshments | |
| 18:00 | Close |